Artificial Intelligence is transforming the way we write code, enabling rapid prototyping and innovation. However, when using AI-generated code—such as outputs from ChatGPT—security is not guaranteed. Blindly integrating this code into your projects can introduce hidden risks, vulnerable dependencies, and compliance issues that might result in costly reworks down the line.
The Hidden Risks of AI-Generated Code
While AI-generated code can speed up development, it may:
- Include outdated or vulnerable libraries and dependencies.
- Contain subtle logic errors or insecure coding patterns.
- Lack proper error handling, input sanitization, or secure authentication.
- Violate licensing terms or introduce compliance issues.
In short, AI-generated code should be audited as carefully as any manually written code.
Actionable Steps to Automate Code Auditing in Your DevOps Pipeline
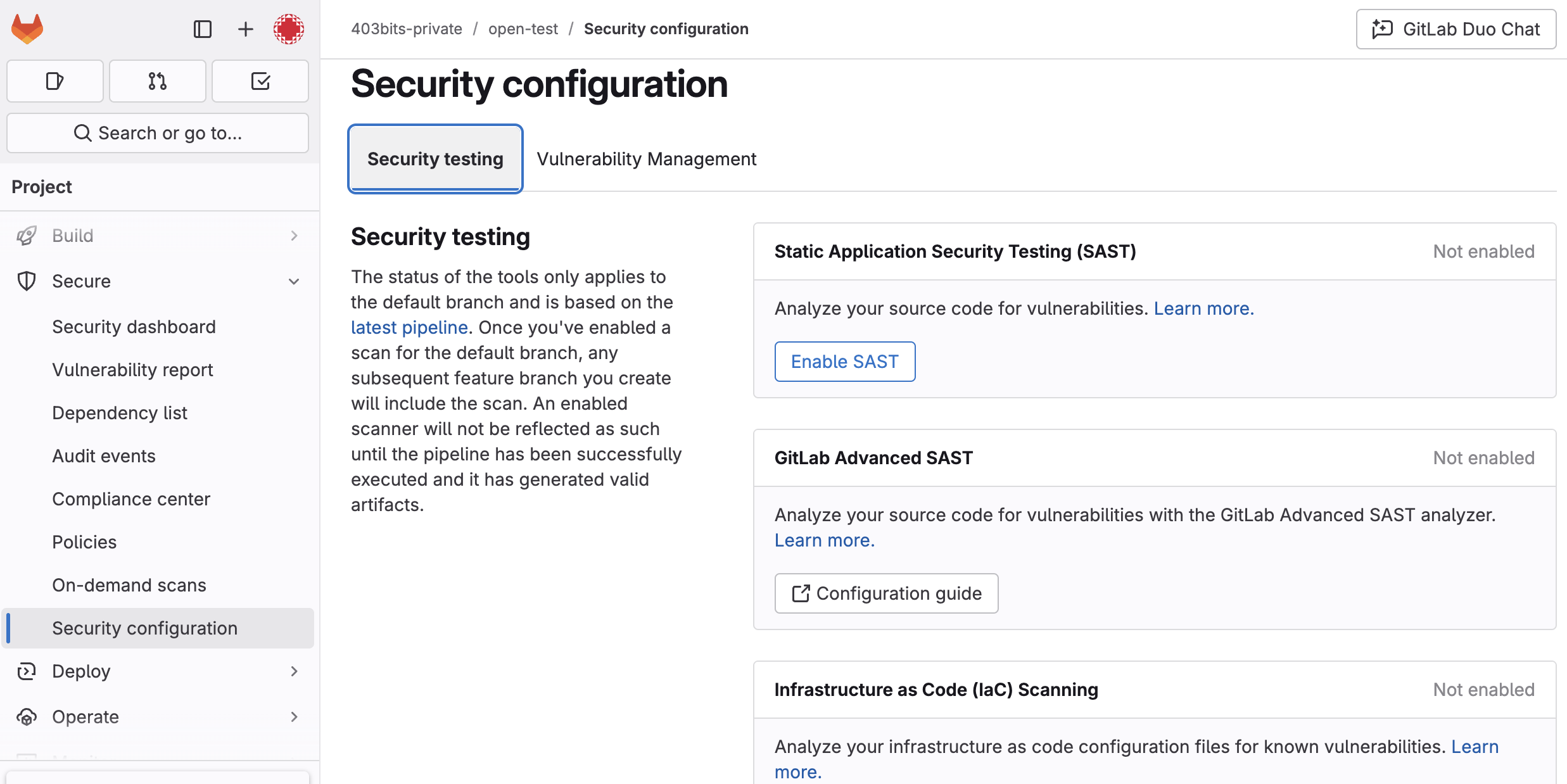
Integrating automated security and dependency audits into your CI/CD pipelines can help catch these issues early. Here’s how you can do it with GitLab's native functionality and integrations:
1. Integrate Static Application Security Testing (SAST)
Leverage GitLab’s built-in SAST to analyze AI-generated code for security vulnerabilities. Enable SAST in your project to scan your source code and produce actionable reports.
Quick Win: Simply add GitLab's SAST template to your .gitlab-ci.yml file:
include:
- template: Security/SAST.gitlab-ci.yml
This inclusion triggers a series of static analysis tools that evaluate your code for insecure patterns and potential risks.
2. Perform Dependency Scanning
AI-generated code often pulls in libraries and dependencies. Vulnerable or outdated dependencies can be a major security risk. GitLab’s dependency scanning feature automates this process.
Quick Win: Incorporate the dependency scanning template:
include:
- template: Security/Dependency-Scanning.gitlab-ci.yml
This ensures that every commit is checked for vulnerable dependencies and alerts you if a risky package is included.
3. Automate Dynamic Application Security Testing (DAST)
Once your AI-generated code is deployed to a staging environment, use DAST to detect vulnerabilities that only appear at runtime. GitLab provides DAST functionality to continuously monitor your application’s behavior.
Quick Win: Configure a DAST job in your CI/CD pipeline:
dast:
stage: test
image: registry.gitlab.com/gitlab-org/security-products/dast:latest
variables:
DAST_WEBSITE: "http://staging.example.com"
script:
- echo "Running DAST on staging environment..."
- dast --target "$DAST_WEBSITE"
artifacts:
reports:
dast: gl-dast-report.json
only:
- master
This setup scans your running application, identifying issues like misconfigurations and runtime vulnerabilities that static analysis might miss.
4. Use Code Quality Tools and Automated Linters
Code quality tools can flag insecure coding practices and potential errors. While these may not catch every security flaw, they are a critical first line of defense.
Quick Win: Integrate tools like ESLint, Pylint, or RuboCop into your pipeline. For instance, a simple job for JavaScript projects could look like this:
code_quality:
stage: test
image: node:14
script:
- npm install
- npx eslint . --format json -o eslint-report.json
artifacts:
paths:
- eslint-report.json
only:
- merge_requests
This job ensures that your code adheres to best practices and highlights potential issues early in the development cycle.
5. Educate and Automate Remediation for Rapid Iteration
While tools can catch many issues, educating your team on the risks associated with AI-generated code is equally important. Implement automated workflows to notify developers of vulnerabilities and even create remediation tasks.
Quick Win: Use GitLab’s Security Dashboard and custom scripts to create issues for detected vulnerabilities automatically. For example, a Python script integrated into your pipeline can trigger GitLab’s API:
# Example: trigger_vulnerability_remediation.py
import requests, os
GITLAB_API_URL = os.environ.get('CI_API_V4_URL')
PROJECT_ID = os.environ.get('CI_PROJECT_ID')
PRIVATE_TOKEN = os.environ.get('GITLAB_PRIVATE_TOKEN')
def create_issue(vulnerability):
url = f"{GITLAB_API_URL}/projects/{PROJECT_ID}/issues"
data = {
'title': f"Remediate vulnerability: {vulnerability}",
'description': f"A vulnerability has been detected: {vulnerability}. Please investigate and remediate.",
'labels': 'security,automated'
}
headers = {'PRIVATE-TOKEN': PRIVATE_TOKEN}
response = requests.post(url, data=data, headers=headers)
if response.status_code == 201:
print(f"Issue created for vulnerability: {vulnerability}")
else:
print("Failed to create issue:", response.text)
# Example usage:
create_issue("Potential SQL Injection in AI-generated query builder")
This script can be triggered as part of your remediation pipeline, ensuring that security issues are tracked and addressed promptly.
Best Practices and Modern Approaches
To maximize the security of AI-generated code, consider the following best practices:
- Never Trust the Output: Always treat AI-generated code as a first draft that needs to be audited and improved upon.
- Integrate Multiple Security Scanners: No single tool catches all issues; combine SAST, DAST, dependency scanning, and code quality tools for comprehensive coverage.
- Adopt a Continuous Feedback Loop: Use GitLab’s dashboards to monitor security metrics continuously and adjust your pipelines based on emerging threats.
- Invest in Developer Training: Regularly update your team on the latest security practices and common vulnerabilities, particularly those associated with AI-generated code.
Conclusion
AI-generated code offers tremendous benefits in terms of speed and innovation, but it also comes with hidden risks. By automating security audits, dependency scanning, and code quality checks through GitLab’s native CI/CD pipelines, you can mitigate these risks and safeguard your projects from costly future reworks and compliance issues.
Comprehensive, multi-layered approach not only protects your code and infrastructure but also fosters a culture of security and continuous improvement—essential for any startup looking to innovate safely.
Start integrating these automated practices today and ensure that your rapid prototyping doesn’t come at the cost of your organization’s security and long-term success.