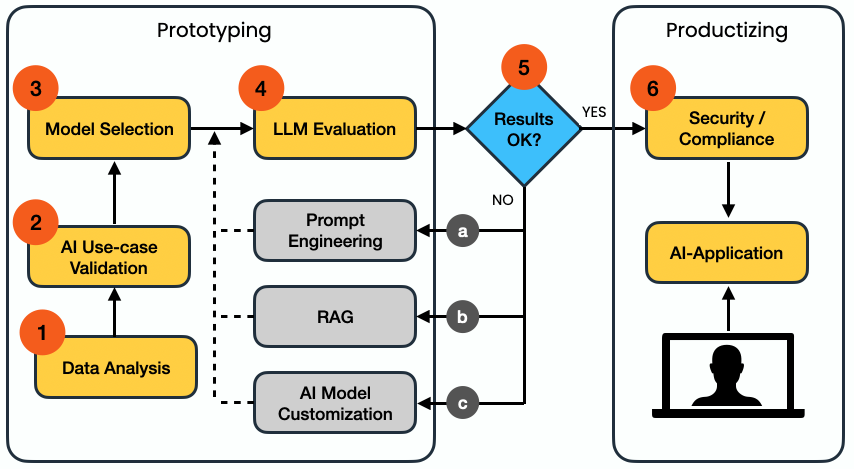
We help you evaluate and plan AI integration opportunities that align with your business objectives and security requirements.
-
AI Feasibility Analysis
Comprehensive evaluation of your business processes to identify high-impact opportunities for AI integration, considering technical feasibility, ROI, and risk factors.
-
AI Integration Roadmap
Development of a structured implementation plan that prioritizes quick wins while building towards long-term AI capabilities, with clear milestones and success metrics.
-
Cost-Benefit Analysis
Detailed assessment of implementation costs, potential benefits, and ROI projections for proposed AI initiatives, helping you make informed decisions.
We implement secure and efficient AI solutions, leveraging both local and cloud-based Language Learning Models (LLMs) to enhance your operations.
-
Local LLM Deployment
Implementation of on-premises AI models that ensure data privacy and reduced latency for sensitive operations, with proper security controls and monitoring.
-
Cloud LLM Integration
Secure integration of cloud-based AI services (like GPT, Claude, or Gemini) with appropriate data protection measures and cost optimization strategies.
-
Custom AI Model Development
Development and fine-tuning of AI models specific to your business domain and use cases, ensuring optimal performance and accuracy.
We ensure your AI implementations adhere to security best practices and compliance requirements while protecting sensitive data.
-
AI Security Guardrails
Implementation of robust security controls for AI systems, including data sanitization, prompt injection prevention, and output validation to prevent misuse and ensure reliable operation.
-
Data Privacy Controls
Setup of comprehensive data protection measures for AI operations, ensuring compliance with GDPR and other relevant regulations while maintaining AI effectiveness.
-
AI Risk Management
Continuous monitoring and assessment of AI operations to identify and mitigate potential risks, ensuring responsible and ethical AI use.
We support the roll-out, integration and onboarding of AI-driven automation solutions with your team.
-
Integration and Testing
Seamless integration of AI automation with existing systems and thorough testing to ensure reliability and accuracy.
-
Workflow Optimization
Detailed mapping of business processes to identify automation opportunities and design optimal AI-enhanced workflows.
-
User Trainings and Support
Comprehensive training programs and ongoing support to ensure your team can effectively use and manage AI solutions.