GitLab is a powerful platform that integrates version control, CI/CD, and security features all in one place. However, its flexibility means that misconfigurations can easily slip in, creating significant security blind spots. In this article, we’ll dive into some of the most common and painful GitLab misconfigurations, illustrate with examples and code snippets, and provide actionable advice on how to fix them.
1. Overly Permissive Project Visibility
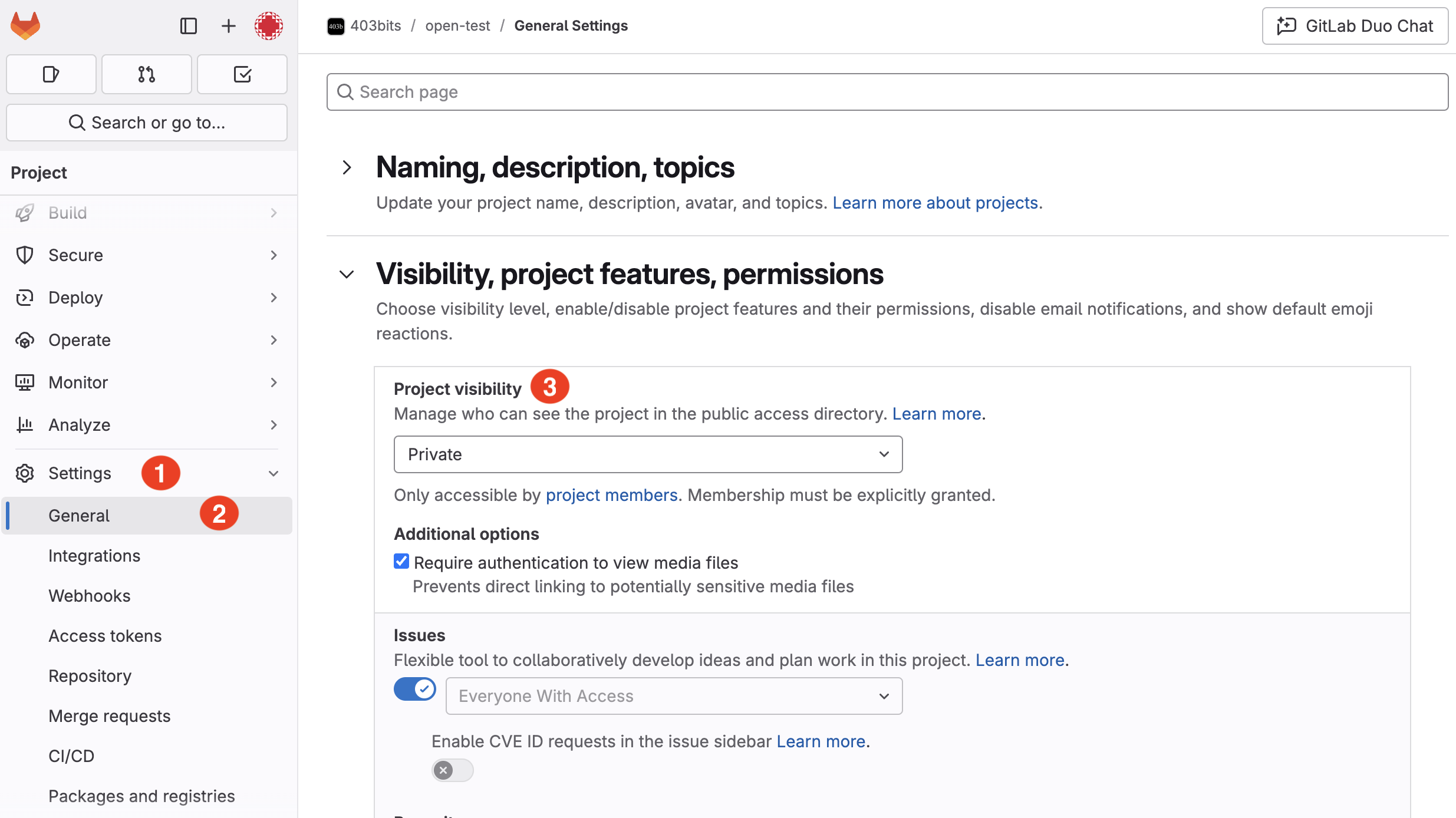
Issue: Setting your project to public when it contains sensitive information can expose your code and configuration files to the world.
Example: A repository set to "Public" might inadvertently reveal secrets in configuration files, API keys, or internal documentation.
Quick Fix: Review your project settings and adjust the visibility to "Private" or "Internal" as appropriate. In GitLab, navigate to Settings > General > Visibility, project features, permissions and change the project’s visibility level.
2. Insecure CI/CD Runner Tokens
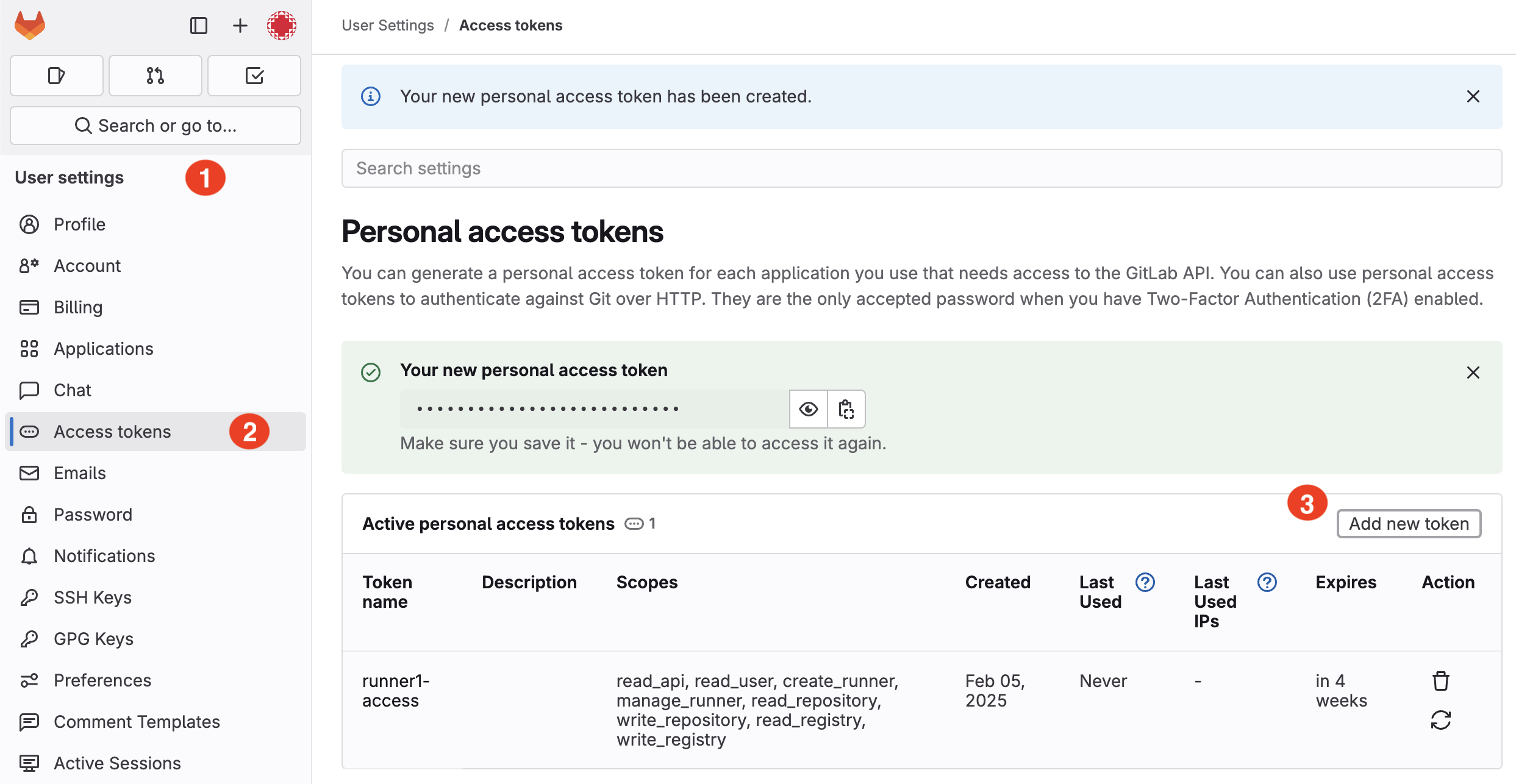
Issue: Misconfiguring your CI/CD runners or exposing runner tokens can allow unauthorized users to execute arbitrary code on your build infrastructure.
Example: Storing runner tokens in public repositories or not rotating them regularly increases the risk of token misuse.
Quick Fix: Ensure that runner tokens are stored securely using GitLab’s protected variables and secrets management. Additionally, configure runners to only run jobs from trusted projects.
3. Misconfigured Protected Branches
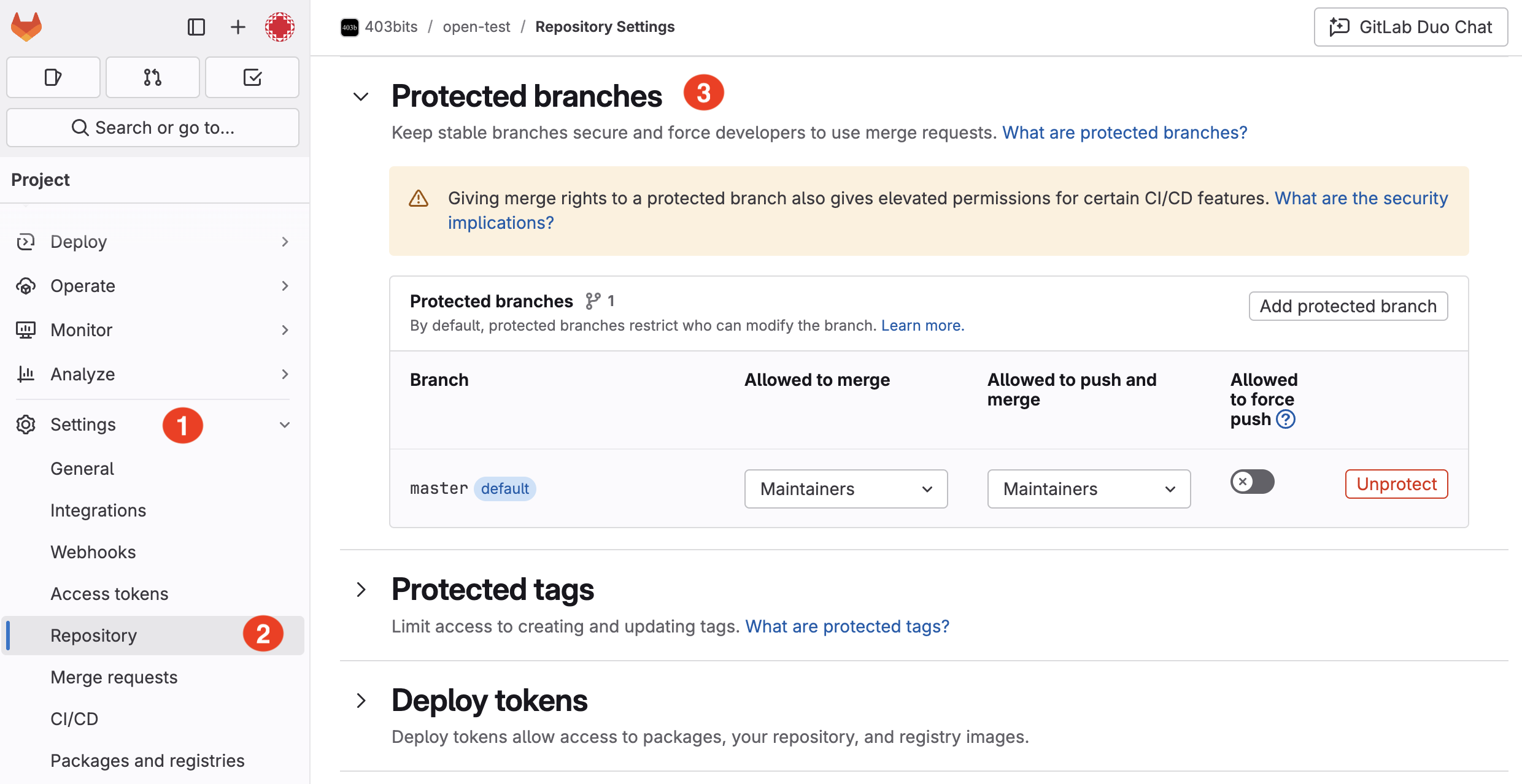
Issue: Failing to properly protect important branches (like main or master) can allow unauthorized merges, bypassing review processes.
Example: If the main branch isn’t protected, a developer might accidentally push unreviewed or insecure code directly into production.
Quick Fix: In your GitLab project, navigate to Settings > Repository > Protected Branches and configure the rules so that only specific roles or pipelines can merge changes into critical branches.
4. Exposing Sensitive CI/CD Variables
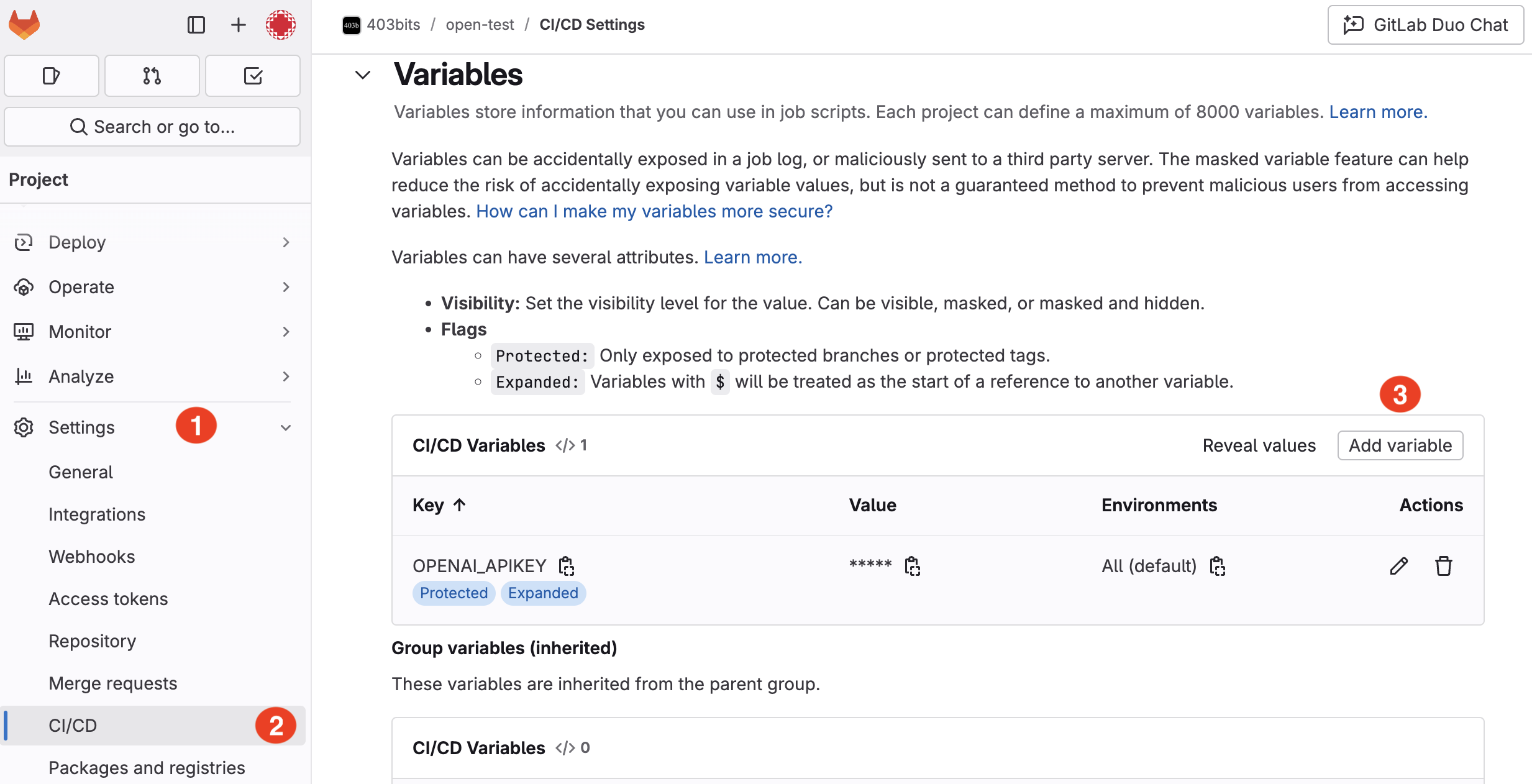
Issue: CI/CD pipelines often rely on environment variables for API keys, tokens, and other secrets. If these variables are not properly secured, they might be exposed in job logs or through misconfigured permissions.
Example: A misconfigured variable might be set to "public" instead of "protected", allowing it to be seen in job output.
Quick Fix: Always mark sensitive variables as "protected" in your GitLab CI/CD settings. Review your .gitlab-ci.yml file and ensure that secrets are not echoed in your logs. For example:
# .gitlab-ci.yml snippet for handling secrets securely
stages:
- build
- deploy
deploy_job:
stage: deploy
script:
- echo "Deploying application..."
only:
- main
variables:
# Ensure sensitive variables are protected and not printed in logs
API_KEY: $API_KEY_PROTECTED
5. Inadequate Access Controls for Group and Project Members
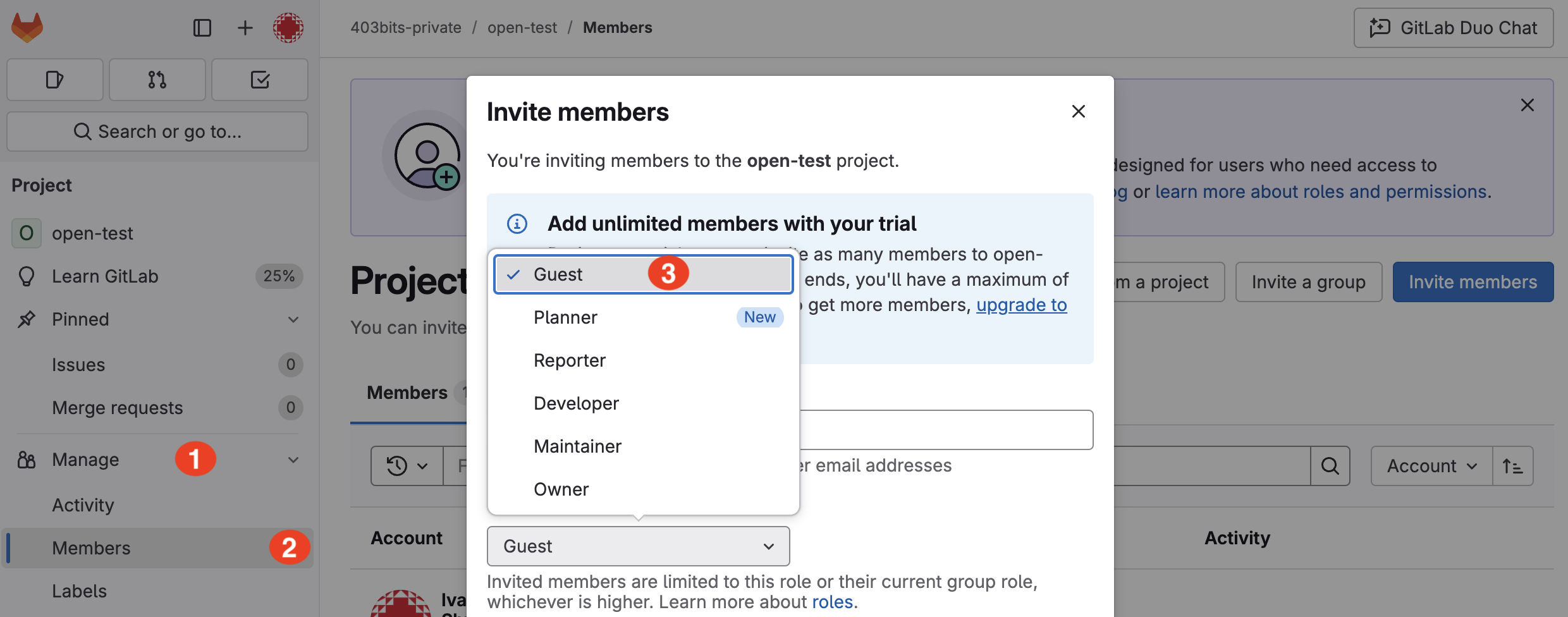
Issue: Granting more permissions than necessary (e.g., Developer instead of Reporter) can lead to accidental or intentional misuse of project resources.
Example: A developer with write access might accidentally push insecure code, or a misconfigured group setting might expose repositories to the wrong users.
Quick Fix: Regularly review and audit user roles in your GitLab groups and projects. Limit permissions to the minimum required level. Use GitLab’s Audit Events feature to track changes in access control settings.
6. Unsecured Webhooks and Integrations
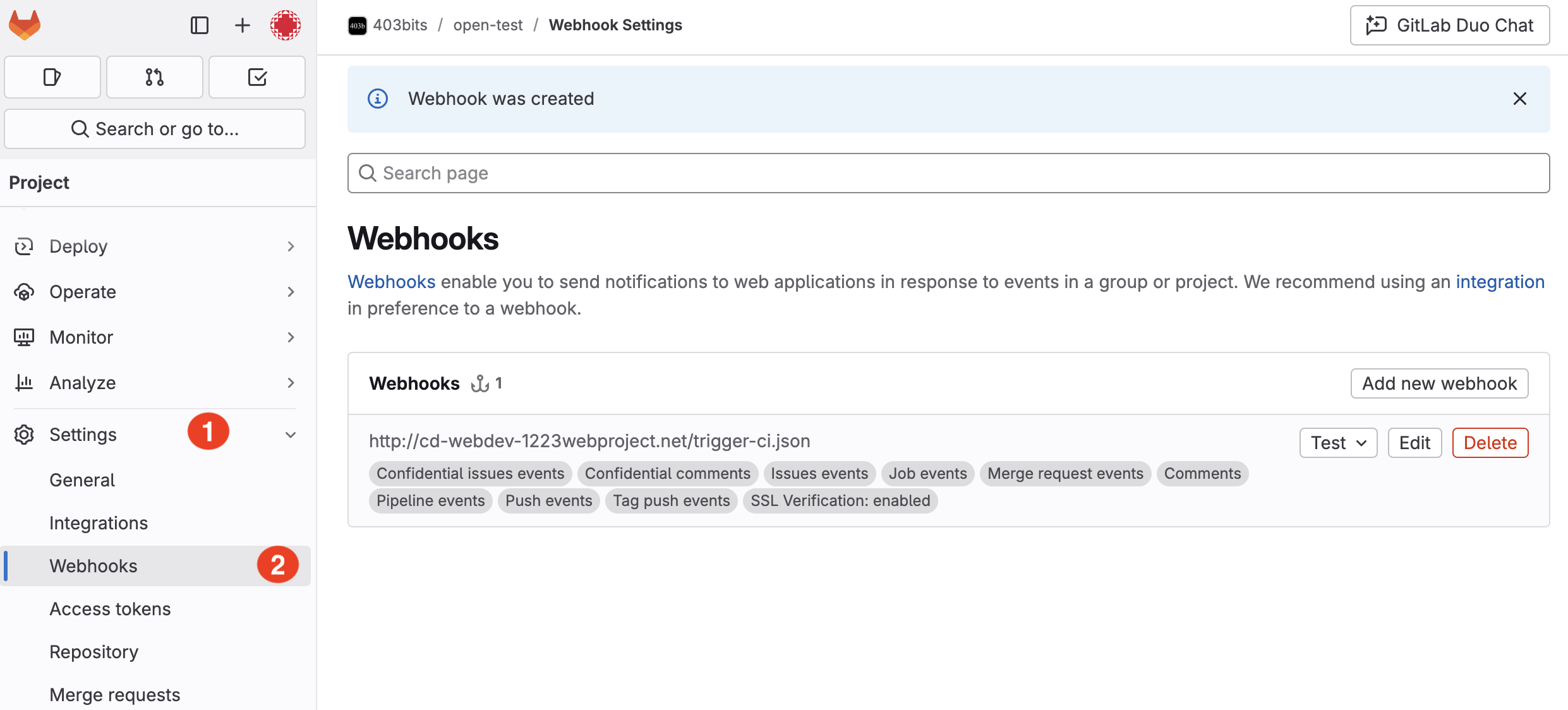
Issue: Webhooks and integrations can be a weak link if not secured properly. Without proper validation, they can be exploited to send unauthorized commands or data.
Example: An unsecured webhook might allow an attacker to trigger CI/CD jobs or access sensitive information.
Quick Fix: Always secure your webhooks by validating payloads with a secret token. Configure your webhook settings in GitLab to include a secret token and verify it in your integration’s endpoint.
Final Thoughts
Misconfigurations in GitLab can lead to serious security blind spots, potentially exposing your code, secrets, and infrastructure to risk. By understanding and addressing these common issues—such as overly permissive visibility, insecure CI/CD configurations, and weak access controls—you can significantly enhance the security of your GitLab environment.
Regular audits, clear policies, and secure configuration practices are key to maintaining a robust and secure CI/CD pipeline. Stay vigilant and update your configurations as your project evolves to minimize risks.